Portfolios
Cloud Security - Hijacking of services …
Cloud computing represents a field currently in great expansion which includes many challenges, especially in terms of security. In fact, many companies use cloud computing as a tool to store their data. Or more of these data include sensitive or important information that needs to be kept away from malicious users. However, this environment remains at risk of attacks such as service and account hijacking attacks. So in this article, we seek to determine whether the AWS security recommendations …
Co-simulation of a Road Infrastructure …
With the modernization of modes of transportation came the automobile, and with it came the road system used by billions of people who rely on it to get from point A to point B as safely and efficiently as possible. From a cyberterrorism perspective, this infrastructure is a prime target, and it is appropriate to question the vulnerabilities that could exist there. A disruption of confidentiality, integrity, and/or availability, three essential pillars of cybersecurity, could have catastrophic …
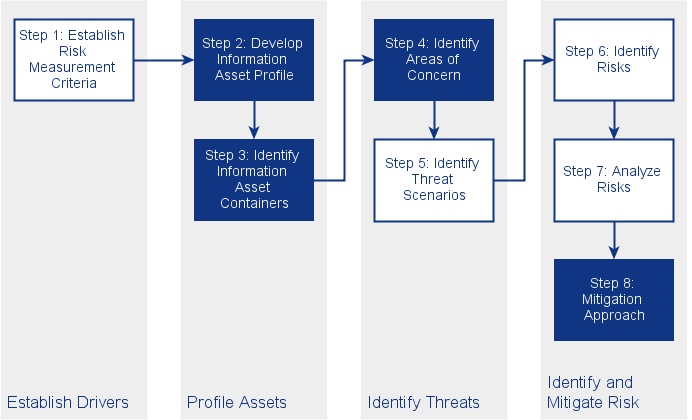
Risk Analysis of a Fake Company Using …
LaForêt (a fictional company) faces new challenges due to evolving cyber risks. Despite the increased visibility of cybersecurity incidents, most organizations, including LaForêt, continue to view the cost of security as a necessary evil rather than an investment. As a consultant, you have undertaken to present to LaForêt a cyber risk assessment to which the cooperative is exposed. Your analysis must make it possible to better explain the risks to the executive, and make better decisions to …
Cloud Security - Comparative Critique of …
Throughout the years, cloud infrastructures have been taking a bigger role and importance with companies favoring and promoting the usage of the cloud instead of on-premise infrastructures. This has pushed for a higher need for better services and management of cloud infrastructures, without forgetting the security aspects of having an your whole organization relying on a setup accessible by public internet (public cloud). With this massive move to the cloud, multiple researches have been made …